Starting with Windows Server 2012 ESU (Extended Security Updates), Microsoft introduced the option to utilize Azure Arc for licensing and payment of ESUs. This approach offers numerous advantages, and I find few drawbacks apart from the need for secure usage of Azure Arc. It’s clear that Microsoft aims to encourage the use of Azure Arc for On-Premises servers to gain insights into the actual infrastructure running on these machines. This approach could simplify future billing processes, ensuring charges align closely with actual usage, eliminating reliance on honor-based estimations or costly audits.
The benefits of opting for this licensing model for ESUs include:
- Monthly Payment Structure: Payment is on a monthly basis, eliminating the need for upfront costs.
- Pay-As-You-Go: Payment is based on actual usage each month. When decommissioning machines, updating licenses in Azure results in reduced payments, ensuring costs reflect current infrastructure accurately.
- Corporate Azure Rebates: Enterprises with corporate rebates on Azure prices also enjoy these benefits extended to ESU licensing, potentially reducing overall costs.
- Elimination of Annual Deployment: Unlike traditional licensing models requiring yearly deployments for patches, this model potentially streamlines and eliminates the need for such frequent deployments, easing administrative burdens.
Licences Pack
If these reasons resonate with you and maintaining a new agent value less than those benefits, here are some suggested instructions I recommend following :
- Verify that your Non-Prod servers comply with the criteria outlined to qualify for the free ESU Licenses (refer to https://learn.microsoft.com/en-us/azure/azure-arc/servers/deliver-extended-security-updates#additional-scenarios).
- Generate an ESU License for each scenario that meets these criteria. Remember to apply the appropriate tag to ensure exemption from charges.
- Issue an ESU License for DataCenter licenses utilized for VM Hosts, considering the cost efficiency between DataCenter and Standard Licenses based on the number of VM cores and licenses used.
- Issue an ESU License for DataCenter licenses applied to physical Windows servers, if this scenario is applicable within your organization’s infrastructure.
- Issue an ESU License for Standard licenses used on physical servers, if this scenario is relevant within your organization’s setup.
Azure Connected Machine Agent (Arc Agent)
- Install the Azure Connected Machine Agent on the Windows 2012 boxes (in this example) and deploy it using your preferred tool.
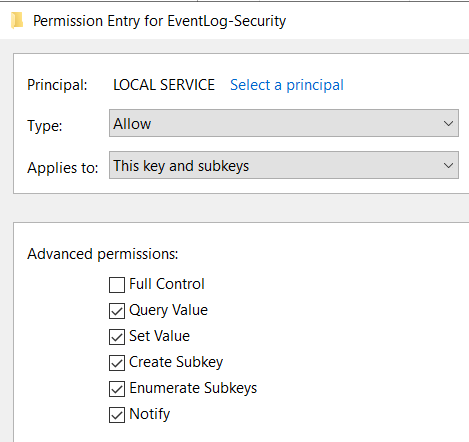
- Ensure the security of the Azure Connected Machine Agent by taking these steps:
- Disable the guest configuration extension to prevent unauthorized access or alterations via Azure Policy. Only individuals with Administrative privileges on the machine should be able to affect it. Command: azcmagent config set guestconfiguration.enabled false
- Set the default value to disallow extensions, allowing specific extensions selectively to maintain control over what runs on your machine. Command: azcmagent config set extensions.allowlist « Allow/None »
- Disable the capability to install new extensions. Command: azcmagent config set extensions.enabled false
Implementing these configurations helps maintain tight control over access and extensions on your machines while using the Azure Connected Machine Agent. »
Securing the Azure Connected Machine Agent is crucial to prevent potential escalation paths from Azure to On-Premises environments. Consider the scenario where an improperly configured agent could allow a contributor in the subscription where Arc-enabled machines are set up to execute commands, potentially gaining Administrator rights on your machines like in this example :
Connect-AzAccount
$auth = Get-AzAccessToken
$AuthenticationHeader = @{
"Content-Type" = "application/json"
"Authorization" = "Bearer" + $auth.Token
}
$requestURL = "https://management.azure.com/subscriptions/yoursubscriptionid/resourceGroups/yourressourcegroup/providers/Microsoft.HybridCompute/machines/theservername/runCommands/YourScriptName?api-version=2023-10-03-preview"
$body = @"
{
"location":"yourregion",
"properties":{
"source":{
"script":"Add-LocalGroupMember -Group 'Administrator' -Member 'YourDomain\TheUserName'"
}
}
}
"@
Invoke-RestMethod -Uri $requestURL - Headers $AuthenticationHeader -Method PUT -Body $bodyConfiguration
- Configure or deploy the settings of the Arc subscription to the Azure Connected Machine Agent.
- Associate the machines with the appropriate ESU licenses.
- Deploy KB5017220 to enable Windows 2012 ESU patches (refer to: https://support.microsoft.com/en-us/topic/kb5017220-update-for-the-extended-security-updates-licensing-preparation-package-for-windows-server-2012-r2-f07633ae-5383-44f8-a444-38448a66a958).
Here’s some lines that you can use to update the licences core number, so you get the benefits of the Pay as you go :
Connect-AzAccount
$auth = Get-AzAccessToken
$AuthenticationHeader = @{
"Content-Type" = "application/json"
"Authorization" = "Bearer" + $auth.Token
}
$requestURL = "https://management.azure.com/subscriptions/yoursubscriptionid/resourceGroups/yourressourcegroup/providers/Miccrosoft.HybridCompute/licenses/YourLicencePackageName?api-version=2023-06-20-preview"
$body = @"
{
"location":"yourregion",
"type":"Microsoft.HybridCompute/licenses",
"properties":{
"tenantid":"yourtenantid",
"licenseType":"ESU",
"licenseDetails":{
"state":"Activated",
"target":"Windows Server 2012",
"edition":"youredition",
"type":vCore",
"processors":yournewvalue
}
}
}
"@
Invoke-RestMethod -Uri $requestURL - Headers $AuthenticationHeader -Method PUT -Body $bodyThis method holds promise not only for Windows 2012 ESU patches but also for forthcoming ESUs offered by Microsoft, particularly beneficial for products like SQL Server and other associated ESUs.