In this blog post i list the essential features a server environnement should have to be considered almost perfect :
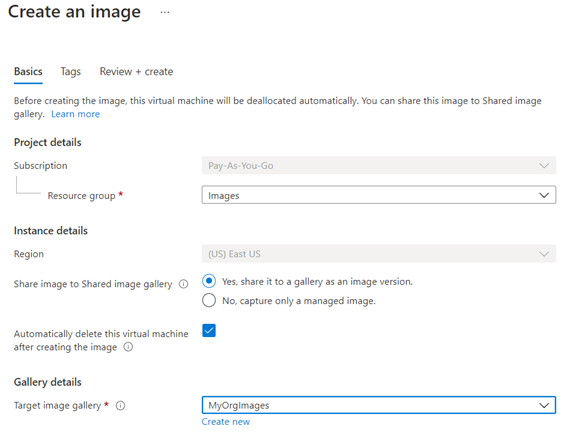
- 100 % automated image build and deploy to a store (Azure compute gallery, VmWare Content library, etc.).
- 100 % automated server build mechanism, so no humain is involve for the server delivery.
- 100 % automated server destruction mechanism.
- Servers are shut down when not in use to save energy, hosts shut down, save cost in cloud.
- Servers capacity are well used, right-sizing, automated size reviews, storage sizing, storage tier (archive, cold, hot, performance), tier reviews and auto-adjust, scheduled.
- Predictable stability, i mean that if your servers are all built the same way, same tools, same versions, you then are in control of the environnement where you do modifications, you just have to take the software exceptions into account.
- All the server function/roles are deploy automated, so you can rebuild the server if needed, you can migrate OS with a high level of confidence .
- Receipes of auto-adaptability of most of the scenarios that your entreprise can have, ex. auto-storage provisionning in a controled environnement if batch need it, end of month CPU needed for some compliance reports
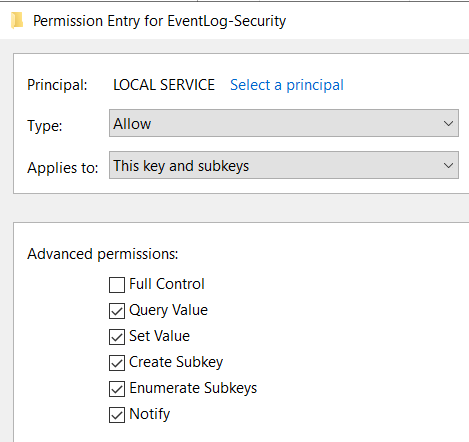
- All (in/out) the network flows are controled and well known, they are validated from the server point of view
- Servers utilization are controled and well known, ex. accounts that authenticate, protocol usage, number of requests per account, per protocol, per port, CPU usage, Memory usage, Network usage
- Servers are 100% compliant to the business standards, all exceptions are documentation into the script that does the validation, this script if auto maintained by automation (server destroy, function/roles deployment) and validate every week.
- All the server functions/roles are tested/monitor with automations, transactions are validated
- All the access to functions/roles support teams are delegated remotly, no interactive logon, so deployment, support logs, software/infrastructure restart are delegated directly or by pipeline.
- The environnement is auto-documented, server names, network flows, servers specs, account access, etc.
In that list i haven’t talk about backup, EDR, SIEM, patches, tooling etc.. only the server functions. We should take server management to a level where we almost never have to log to a server