New capability to manage Device Code authentication in Entra ID. Here, I’ll show you how you can allow Device Code authentication only to a group that you need to Privileged Identity Management (PIM), a Privileged Access Group. So, unless you PIM this group, you won’t be able to use Device Code authentication. Device Code authentication is often used in phishing campaigns and poses a real risk to tenant security. Microsoft has listened to the user community and now brings the ability to manage who can use Device Code. Here, I’ll show you how I would implement this new capability.
Prerequisites :
- Privileged Role Administrator
- Entra ID Premium P2 licence
- Conditional Access Administrator
Create a Security Group
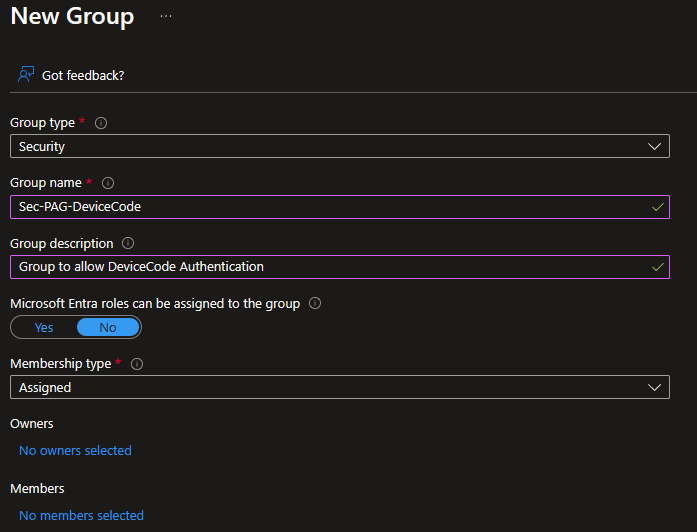
Convert the group as a Privileged access group
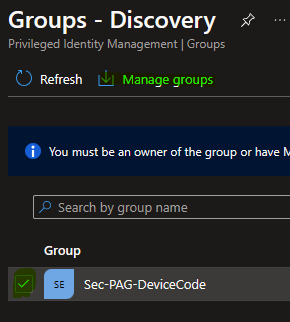
Assign users and configure settings for this group, you can configure allowed time (1 hour should be correct), required MFA
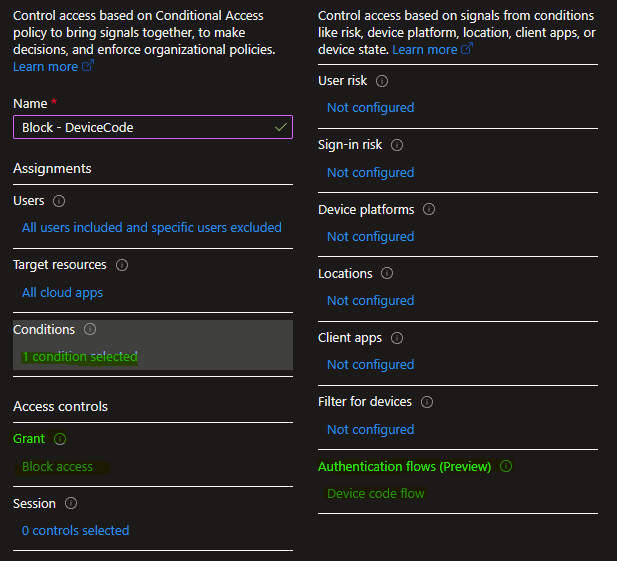
Create a Conditional Access Policy
Include All Users, Exclude your Break the glass accounts and the PAG you previously created
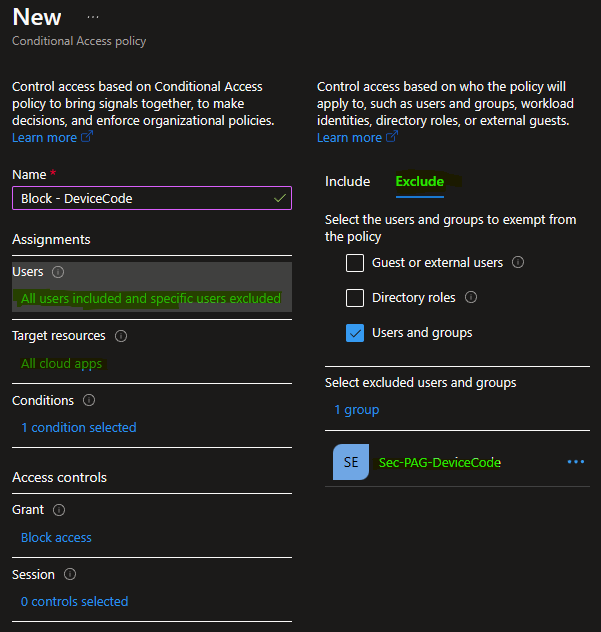
Add the Conditions for Authentication flows – Device code flow
Grant the Block Access
You are now done, so users assigned to this group now need to use Privileged Identity Management to PIM the Security Group to be allowed to use Device Code authentication.